SearchGuard is a security system that can be used to protect Elasticsearch clusters.
When secured, a cluster requires the use of keystores, truststores, and user / password authentication to be accessed.
This article demonstrates how to connect to this kind of clusters in Stambia DI.
Prerequisites:
- addons.elasticsearch_1.0.4.201612161602 or higher
Installation of libraries
The first step is to install in the Runtime the Elasticsearch and SearchGuard libraries.
We cannot provide the exact list of libraries as it depends on the Searchguard and Elasticsearch versions.
But, make sure to use the same libraries versions between Elasticsearch and SearchGuard
Copy all those libraries in the <stambiaRuntime>/lib/addons/elasticsearch folder.
Then restart the Runtime.
As an example, here are the libraries for the 2.4.1 version of Elasticsearch / SearchGuard
apache-log4j-extras-1.2.17.jar
commons-cli-1.3.1.jar
compiler-0.8.13.jar
compress-lzf-1.0.2.jar
elasticsearch-2.4.1.jar
guava-18.0.jar
HdrHistogram-2.1.6.jar
hppc-0.7.1.jar
jackson-core-2.8.1.jar
jackson-dataformat-cbor-2.8.1.jar
jackson-dataformat-smile-2.8.1.jar
jackson-dataformat-yaml-2.8.1.jar
jna-4.1.0.jar
joda-convert-1.2.jar
joda-time-2.9.4.jar
jsr166e-1.1.0.jar
jts-1.13.jar
log4j-1.2.17.jar
lucene-analyzers-common-5.5.2.jar
lucene-backward-codecs-5.5.2.jar
lucene-core-5.5.2.jar
lucene-grouping-5.5.2.jar
lucene-highlighter-5.5.2.jar
lucene-join-5.5.2.jar
lucene-memory-5.5.2.jar
lucene-misc-5.5.2.jar
lucene-queries-5.5.2.jar
lucene-queryparser-5.5.2.jar
lucene-sandbox-5.5.2.jar
lucene-spatial-5.5.2.jar
lucene-spatial3d-5.5.2.jar
lucene-suggest-5.5.2.jar
netty-3.10.6.Final.jar
netty-buffer-4.0.37.Final.jar
netty-codec-4.0.37.Final.jar
netty-common-4.0.37.Final.jar
netty-handler-4.0.37.Final.jar
netty-tcnative-1.1.33.Fork17-linux-x86_64.jar
netty-transport-4.0.37.Final.jar
search-guard-ssl-2.4.1.16.jar
securesm-1.0.jar
snakeyaml-1.15.jar
spatial4j-0.5.jar
t-digest-3.0.jar
Again this is just an example for the 2.4.1 version, it can vary for other versions.
In most cases, the required libraries can be found in the lib/ folder of the Elasticsearch server installation.
Metadata Configuration
Open the Elasticsearch Metadata and configure it as follow.
- Set the HTTP user and password
- Set the Path Home
- Open the Security tab and fill the Security settings
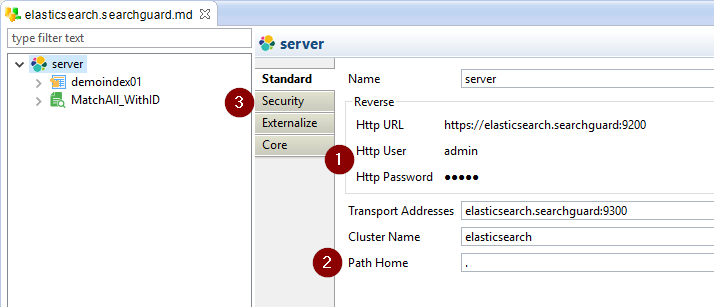
HTTP User and Password
The HTTP user and password will be used when performing reverse operations on the cluster.
This is the login asked when trying to access the cluster from a browser, for instance.
Path Home
The Path Home is the Elasticsearch installation path on the server.
You can use "." to tell the Elasticsearch driver to use the current installation.
Security
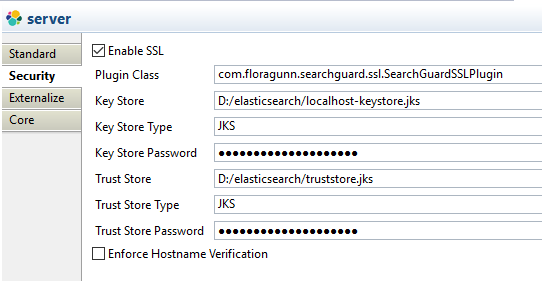
The security settings allow to define the location and properties of the Key Store and Trust Store that will be used by the Runtime when executing Elasticsearch flows.
The Key Store and Trust Store to use are the ones authorized on SearchGuard.
Here is the list of the available Properties:
| Property | Description | Example |
| Enable SSL | Set it to true to enable the security | |
| Plugin Class |
The Java class to use for security. |
For SearchGuard: com.floragunn.searchguard.ssl.SearchGuardSSLPlugin |
| Key Store |
Location of the Key Store file. The Runtime must be able to access it. |
D:/elasticsearch/localhost-keystore.jks |
| Key Store Type | Key Store Type (JKS or PKCS12) | JKS |
| Key Store Password | Password of the Key Store file. | |
| Trust Store |
Location of the Trust Store file. The Runtime must be able to access it. |
D:/elasticsearch/truststore.jks |
| Trust Store Type | Trust Store Type (JKS or PKCS12) | JKS |
| Trust Store Password: | Password of the Trust Store file. |
That's it, Stambia DI is now ready to work with SearchGuard secured Elasticsearch cluster.
You can develop your Mappings and Processes as usual.
The security will be handled by the Metadata and the Runtime.


